Security Testing
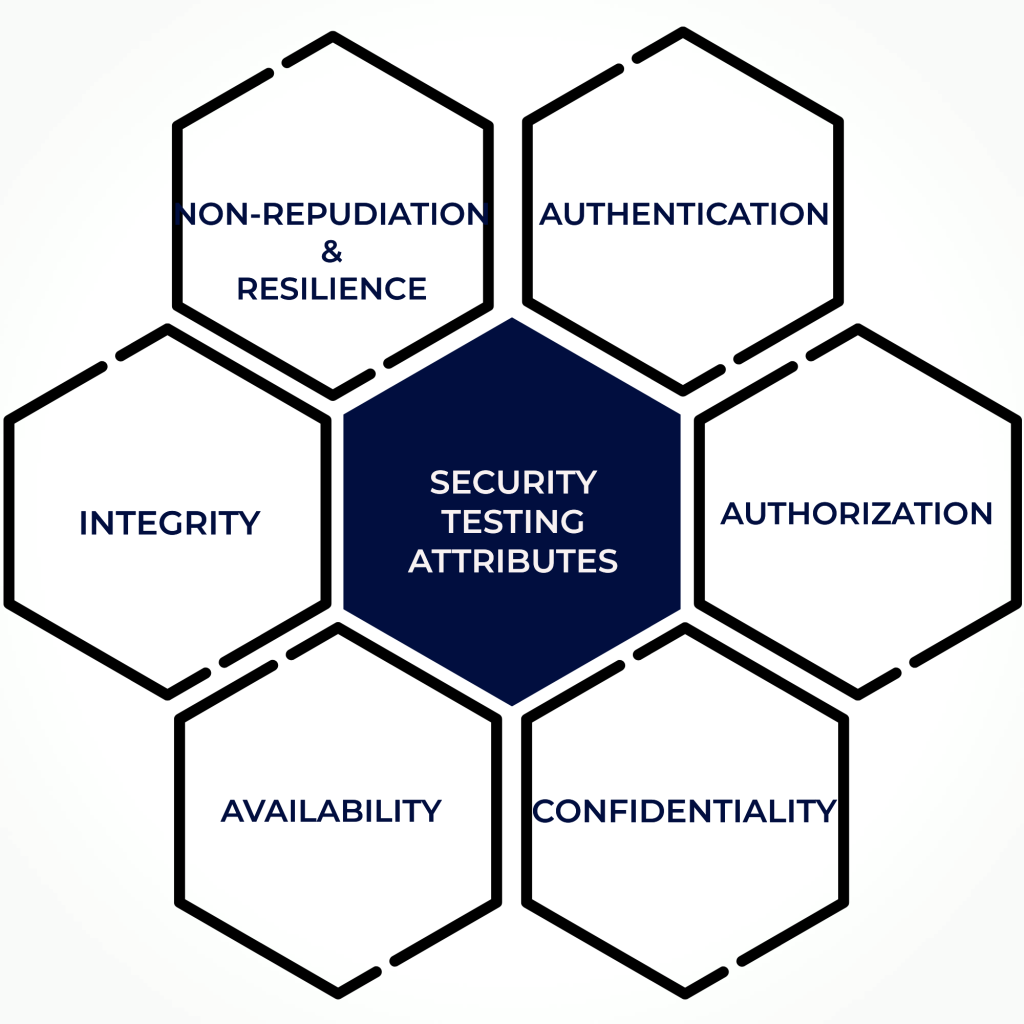
Securing your online platform is essential in today’s digital world and security testing plays an important role in ensuring the safety of your website or application.
It is estimated that over 60% of cyber attacks could have been prevented if proper security testing had been in place. Security testing is a process designed to identify vulnerabilities in an information system and determine the extent to which these vulnerabilities could be exploited by unauthorized users.
Security testing can be divided into two broad categories: vulnerability assessment and penetration testing. Vulnerability assessments are usually conducted by organizations themselves or by independent third-party companies, while penetration tests are typically conducted by specialized security firms.
Vulnerability assessments typically involve the use of automated tools to scan for known weaknesses in systems and applications. Once these weaknesses are identified, they can then be prioritized and remediated accordingly. Penetration tests, on the other hand, are much more targeted and manual in nature. They are designed to simulate real-world attacks against systems and applications in order to assess their security posture.
Our approach
Ensuring Comprehensive Security for Your Software
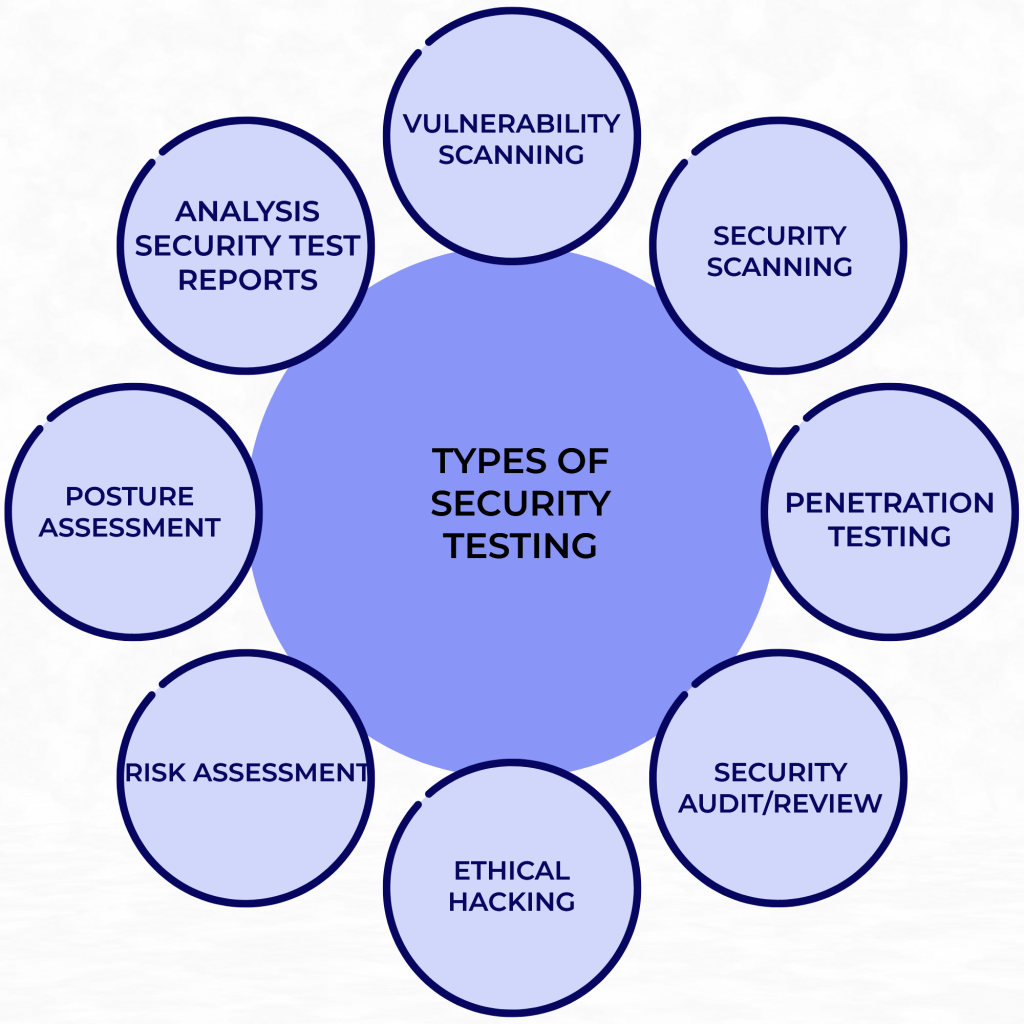
There are many different types of security software testing, each with its own advantages and disadvantages. Here’s a quick overview of some of the most popular types of security testing:
1. Penetration Testing: Also known as “pen testing”, this is one of the most common types of security testing. It involves using various tools and techniques to try and gain unauthorized access to a system. This type of testing can be used to assess both external and internal threats.
2. Vulnerability Scanning: This type of security testing uses automated tools to scan for known vulnerabilities in a system. This can be an effective way to quickly identify potential security issues, but it can’t always find every vulnerability.
3. Security Auditing: A security audit is an independent assessment of a system’s compliance with security policies and procedures. Audits can be used to verify that systems are secure, or to identify areas where improvements are needed.
4. Risk Assessment: A risk assessment is a formal process for identifying and evaluating risks to a system or organization. It’s often used in conjunction with other types of assessments, such as penetration tests or vulnerability scans, to provide a more comprehensive view of risks.
Why DragonFlyTest
- Avoiding major security breaches
- Improving customer confidence
- Complying with regulations
- Building a stronger product
- Identify potential security vulnerabilities in systems and applications
- Simulates an attack on a system to find vulnerabilities
- Manually inspecting code for security issues
- Automated tools to find potential security issues in code
- Static and Dynamic Analysis
From Our Blog Posts
The Importance of Test Planning: Why Skipping it May Cost You More Than You Think
Are you skipping test planning before launching your product? Well, let us tell you that this could cost you more than just a few bucks.
Virtual vs. Real: Which Method Is Best for Testing Mobile Apps?
Mobile apps have revolutionized the way we interact with technology. From hailing a cab to ordering food, everything is just a tap away on our

The Top 5 Benefits of Test Consulting
What is Software Test Consulting? As your business grows, so does the complexity of your software development projects. To ensure that these projects are completed


